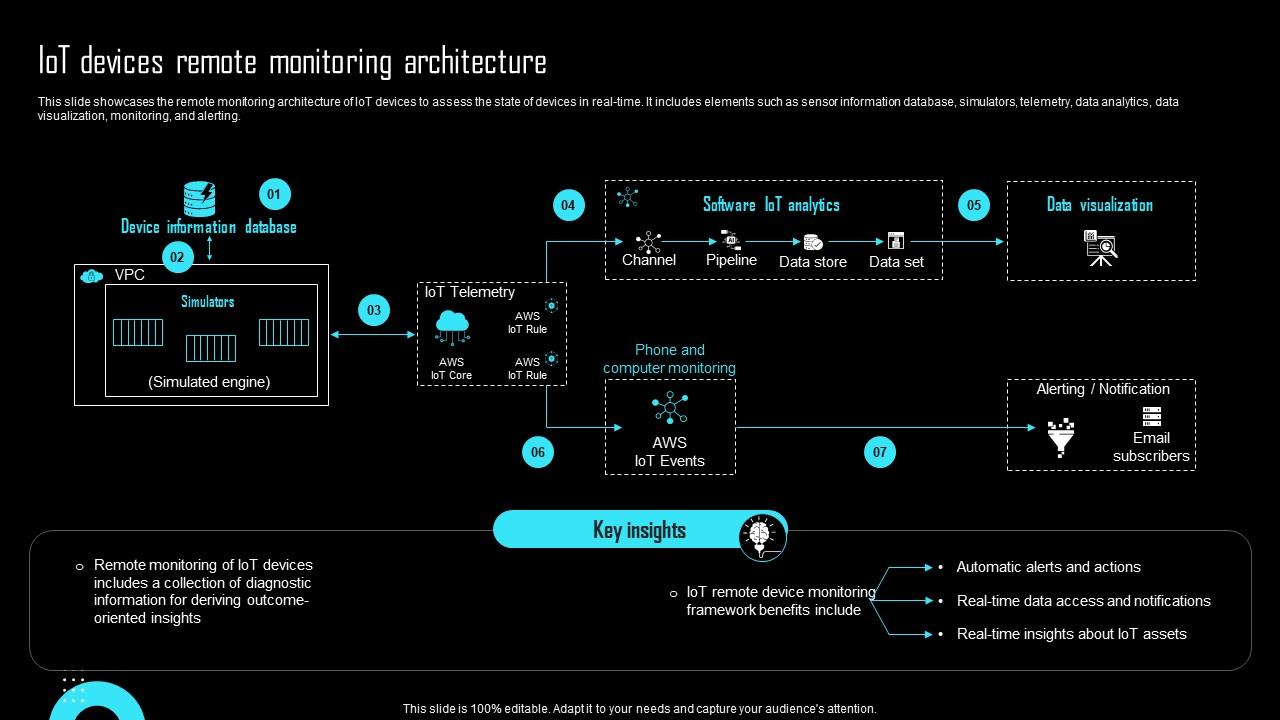
Secure Remote Management IoT Device Examples: Your Ultimate Guide
Let’s face it, the Internet of Things (IoT) is everywhere these days. From smart homes to industrial automation, IoT devices are revolutionizing how we interact with technology. But here’s the catch—securing these devices remotely has become a critical concern for businesses and individuals alike. If you’re wondering how to manage your IoT devices securely, you’ve come to the right place. In this article, we’ll dive deep into secure remote management IoT device examples and give you actionable insights to protect your digital assets.
Imagine this: you’re managing a network of IoT devices spread across different locations. How do you ensure they’re all operating efficiently without compromising security? The answer lies in secure remote management. It’s not just about convenience; it’s about safeguarding your data and maintaining control over your devices, no matter where they are.
In a world where cyber threats are lurking around every corner, secure remote management isn’t optional—it’s a necessity. This article will walk you through real-world examples, best practices, and cutting-edge solutions to help you stay ahead of the game. So, buckle up and let’s get started!
Table of Contents
- What is Remote Management of IoT Devices?
- Why Security Matters in Remote IoT Management
- Examples of IoT Devices That Require Secure Remote Management
- Best Practices for Secure Remote Management
- Top Tools and Platforms for Secure IoT Management
- Common Challenges in IoT Remote Management
- Future Trends in Secure Remote IoT Management
- Real-World Cases of Secure IoT Management
- Data Protection Strategies for IoT Devices
- Wrapping It Up
What is Remote Management of IoT Devices?
Alright, let’s break it down. Remote management in the IoT world refers to the ability to monitor, control, and update IoT devices from a distance. Think about it like this—if you’re running a business with dozens of IoT devices scattered across multiple locations, you don’t want to physically visit each one every time something goes wrong. That’s where remote management comes in. You can troubleshoot issues, push software updates, and even reboot devices—all from the comfort of your office.
But here’s the kicker—just because you can manage devices remotely doesn’t mean it’s safe. Without proper security measures, your IoT network could become a playground for hackers. That’s why secure remote management is such a big deal. It’s not just about convenience; it’s about ensuring your devices and data are protected from unauthorized access.
How Does It Work?
Remote management systems typically use a combination of hardware and software to connect IoT devices to a central management platform. This platform allows administrators to perform various tasks, such as:
- Monitoring device performance in real-time
- Updating firmware and software
- Configuring device settings
- Implementing security protocols
And guess what? These systems can be accessed from anywhere in the world as long as you have an internet connection. Pretty cool, right?
Why Security Matters in Remote IoT Management
Now, let’s talk turkey. Security is the backbone of any IoT system, especially when it comes to remote management. Here’s why:
First off, IoT devices often collect sensitive data, whether it’s customer information, industrial processes, or personal health data. If a hacker gains access to your IoT network, they could steal this data or even take control of your devices. Imagine the chaos that could ensue if someone hacked into a smart traffic system or a hospital’s medical equipment. Scary stuff, huh?
Additionally, IoT devices are often seen as easy targets by cybercriminals. Why? Because many of them lack robust security features out of the box. This makes them the perfect entry point for attackers looking to infiltrate larger networks. That’s why implementing secure remote management practices is crucial to protecting your entire infrastructure.
Examples of IoT Devices That Require Secure Remote Management
So, what kind of IoT devices need secure remote management? The list is pretty extensive, but here are some common examples:
- Smart home devices like thermostats, lighting systems, and security cameras
- Industrial IoT (IIoT) devices used in manufacturing and logistics
- Medical IoT devices such as insulin pumps and remote patient monitoring systems
- Smart city infrastructure like traffic lights and public transportation systems
- Agricultural IoT devices for crop monitoring and irrigation control
Each of these devices plays a vital role in its respective industry, but they all share one thing in common—they need to be managed securely to prevent potential threats.
Real-Life Scenario
Let’s say you’re managing a fleet of smart irrigation systems for a large agricultural company. These systems are spread across hundreds of acres, making it impractical to physically check each one. With secure remote management, you can monitor water usage, adjust settings based on weather conditions, and even detect leaks—all without leaving your desk. Not only does this save time and resources, but it also ensures your crops get the water they need to thrive.
Best Practices for Secure Remote Management
Okay, so you know why secure remote management is important. But how do you actually implement it? Here are some best practices to keep in mind:
1. Use Strong Authentication Methods
Two-factor authentication (2FA) and multi-factor authentication (MFA) should be your go-to security measures. These methods add an extra layer of protection by requiring users to provide more than one form of identification before accessing your IoT network.
2. Encrypt All Communications
Data encryption ensures that even if someone intercepts your communications, they won’t be able to read or use the information. Always use secure protocols like HTTPS and TLS when transmitting data between your devices and management platform.
3. Regularly Update Firmware and Software
Software vulnerabilities are a hacker’s dream come true. To minimize the risk, make sure you’re regularly updating the firmware and software on your IoT devices. Many remote management platforms offer automatic update features, so take advantage of them.
4. Implement Network Segmentation
By dividing your network into smaller segments, you can limit the damage if one segment is compromised. This way, even if a hacker gains access to one part of your network, they won’t be able to move laterally and attack other parts.
Top Tools and Platforms for Secure IoT Management
When it comes to secure remote management, having the right tools and platforms can make all the difference. Here are a few popular options:
- AWS IoT Core: A fully managed service that allows you to securely connect and manage IoT devices at scale.
- Microsoft Azure IoT Hub: A cloud-based solution for managing IoT devices with built-in security features.
- Google Cloud IoT Core: Offers robust security and analytics capabilities for IoT deployments.
- IBM Watson IoT Platform: Combines IoT management with AI-powered analytics for smarter decision-making.
Each of these platforms has its own strengths, so it’s important to choose one that aligns with your specific needs and budget.
Common Challenges in IoT Remote Management
While secure remote management offers numerous benefits, it’s not without its challenges. Here are a few common hurdles you might encounter:
1. Scalability
As your IoT network grows, managing all those devices can become increasingly complex. Ensuring your management platform can scale with your needs is crucial to maintaining efficiency.
2. Connectivity Issues
IoT devices rely on stable internet connections to function properly. If a device loses connectivity, you might not be able to manage it remotely until the issue is resolved.
3. Compliance Requirements
Depending on your industry, you may need to comply with various regulations regarding data privacy and security. Make sure your remote management practices align with these requirements to avoid legal issues.
Future Trends in Secure Remote IoT Management
So, what’s on the horizon for secure remote IoT management? Here are a few trends to watch out for:
1. Edge Computing
Edge computing allows IoT devices to process data locally instead of sending everything to the cloud. This reduces latency and improves security by minimizing the amount of data transmitted over the network.
2. AI and Machine Learning
AI-powered analytics can help detect anomalies in device behavior and alert administrators to potential security threats before they become serious issues.
3. Blockchain Technology
Blockchain offers a decentralized approach to securing IoT networks by creating an immutable record of all transactions and communications between devices.
Real-World Cases of Secure IoT Management
Let’s take a look at some real-world examples of companies successfully implementing secure remote IoT management:
Case Study: Smart City Initiative
A major city implemented a smart traffic management system using IoT devices to monitor traffic flow and adjust signal timings in real-time. By using a secure remote management platform, city officials were able to maintain control over the system and quickly respond to any issues that arose.
Case Study: Healthcare Provider
A healthcare provider deployed a network of IoT devices to monitor patients’ vital signs remotely. Secure remote management ensured that patient data was protected and that devices were always functioning optimally.
Data Protection Strategies for IoT Devices
Data protection is a critical component of secure remote IoT management. Here are a few strategies to consider:
1. Data Minimization
Only collect the data you absolutely need. The less data you store, the lower the risk of a data breach.
2. Access Controls
Limit who can access your IoT data and ensure that only authorized personnel have the necessary permissions.
3. Regular Audits
Conduct regular audits to identify potential security vulnerabilities and address them before they can be exploited.
Wrapping It Up
In conclusion, secure remote management of IoT devices is essential for protecting your digital assets and ensuring your network operates efficiently. By following best practices, leveraging the right tools and platforms, and staying informed about emerging trends, you can stay one step ahead of cyber threats.
So, what are you waiting for? Take action today and start implementing secure remote management practices in your IoT network. And don’t forget to share this article with your friends and colleagues who might benefit from it. Together, we can make the IoT world a safer place!