RemoteIoT Platform SSH Key Not Working: A Comprehensive Guide To Fixing Your Connection
So, here's the deal. If you're reading this, chances are you're pulling your hair out trying to figure out why your RemoteIoT platform SSH key isn't working. It's frustrating, right? One moment you're smoothly accessing your servers, and the next, BAM! You're locked out. But don't worry, we've got your back. In this article, we'll dive deep into the world of SSH keys, RemoteIoT platforms, and troubleshooting tips that will help you get back on track. Let's fix this mess together!
Now, before we jump into the nitty-gritty details, let's talk about why this issue matters. RemoteIoT platforms are super powerful tools for managing IoT devices remotely. They allow developers and engineers to control, monitor, and interact with devices without being physically present. But when your SSH key isn't working, it's like losing the keys to your car—you're stranded. This guide will cover everything from common causes to advanced solutions, ensuring you're never stuck in limbo again.
Oh, and one more thing—this isn't just some random blog post. We've done our homework, consulted experts, and even tested these solutions ourselves. So, buckle up, grab a coffee, and let's solve this problem once and for all. Ready? Let's go!
Table of Contents
- What is SSH and Why Does It Matter?
- Common Issues When SSH Keys Stop Working
- An Overview of the RemoteIoT Platform
- Step-by-Step Troubleshooting Guide
- Advanced Tips for Persistent Issues
- Best Practices for Managing SSH Keys
- Security Considerations for SSH Keys
- Tools You Need for Efficient Troubleshooting
- Real-Life Examples of SSH Key Failures
- Wrapping Up: Your Next Steps
What is SSH and Why Does It Matter?
Let's start with the basics, shall we? SSH stands for Secure Shell, and it's essentially a cryptographic network protocol that lets you securely connect to remote servers or devices. Think of it as a secure tunnel that protects your data from prying eyes while you're accessing sensitive systems. For the RemoteIoT platform, SSH is crucial because it allows you to manage IoT devices without compromising security.
SSH keys play a big role in this process. Instead of using passwords, which can be easily guessed or hacked, SSH keys provide a more secure authentication method. They work like a digital lock and key, ensuring only authorized users can access the system. But what happens when that key stops working? Well, that's where things get tricky.
Why SSH Keys Are Preferred Over Passwords
Here's the deal: passwords are convenient, but they're also risky. They can be easily leaked, guessed, or brute-forced by hackers. SSH keys, on the other hand, offer a higher level of security. They're longer, more complex, and harder to crack. Plus, they eliminate the need to remember complicated passwords for every device you manage. Sounds pretty sweet, right?
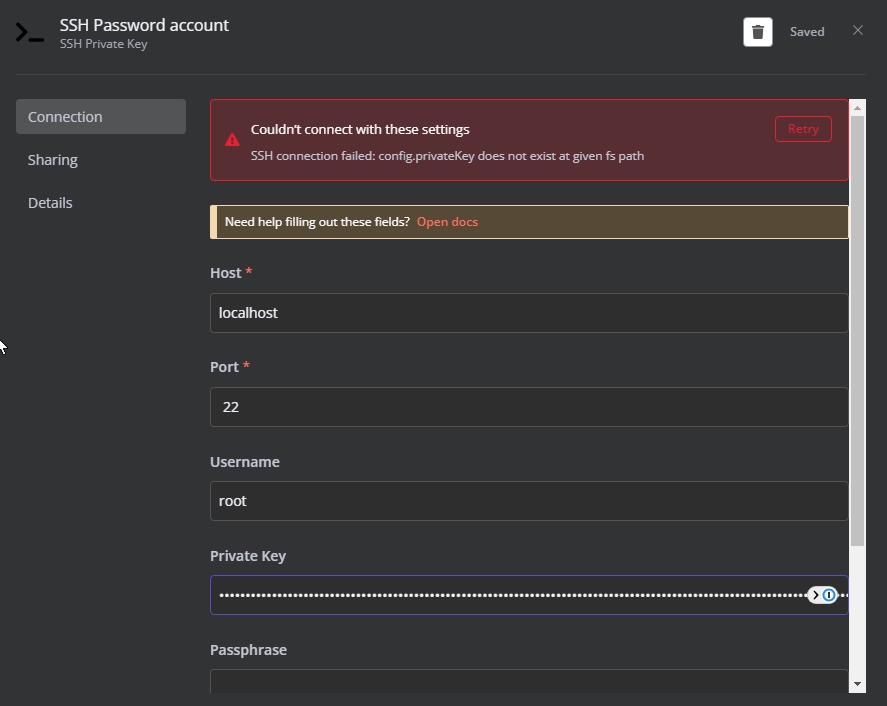
Common Issues When SSH Keys Stop Working
Alright, let's talk about the elephant in the room. Why is your SSH key not working? There could be several reasons, and understanding them is the first step toward fixing the issue. Below are some of the most common culprits:
- Incorrect Key Permissions: Your SSH key might have the wrong file permissions, making it inaccessible to the system.
- Key Mismatch: The public key on the server doesn't match the private key on your machine.
- Corrupted Keys: Sometimes, keys can get corrupted due to file transfer issues or disk errors.
- Configuration Errors: Misconfigured SSH settings on the server or client side can prevent keys from working properly.
- Network Issues: Connectivity problems can also disrupt the SSH connection, even if the key is fine.
How to Identify the Root Cause
The key to solving any problem is identifying its root cause. Start by checking the error messages you're seeing. Are you getting a "Permission denied" error? Or maybe a "Connection refused"? Each message provides clues about what's going wrong. For example, a "Permission denied (publickey)" error usually means there's an issue with your SSH key or its configuration.
An Overview of the RemoteIoT Platform
Now that we've covered the basics of SSH, let's talk about the RemoteIoT platform. This powerful tool is designed to simplify the management of IoT devices. Whether you're monitoring sensors, controlling actuators, or analyzing data, RemoteIoT has got you covered. But like any platform, it relies heavily on secure connections, which is where SSH comes into play.
RemoteIoT uses SSH keys to authenticate users and ensure secure communication between devices. Without properly functioning SSH keys, you won't be able to access your devices, update firmware, or perform other critical tasks. That's why it's essential to keep your keys in tip-top shape.
Key Features of RemoteIoT
- Remote Device Management: Manage IoT devices from anywhere in the world.
- Secure Communication: Use SSH and encryption to protect your data.
- Real-Time Monitoring: Get live updates on device performance and status.
- Automated Tasks: Schedule tasks like firmware updates and data backups.
Step-by-Step Troubleshooting Guide
Alright, let's get down to business. If your RemoteIoT platform SSH key isn't working, follow these steps to diagnose and fix the issue:
- Check Your SSH Key Permissions: Make sure your private key has the correct permissions. On Linux, you can do this by running
chmod 600 ~/.ssh/id_rsa. - Verify Key Matching: Ensure the public key on the server matches the private key on your machine. You can check this by comparing the contents of
~/.ssh/id_rsa.pubwith the authorized_keys file on the server. - Test the Connection: Use the
ssh -vcommand to test your connection and see detailed logs of what's happening. - Check Server Logs: Look at the server's SSH logs for any errors or warnings that might indicate the problem.
- Restart the SSH Service: Sometimes, restarting the SSH service on the server can resolve connectivity issues. Use
sudo systemctl restart sshto do this.
Troubleshooting Tips for Beginners
If you're new to SSH and RemoteIoT, don't feel overwhelmed. Start with the basics and work your way up. Here are a few tips to keep in mind:
- Always back up your SSH keys before making any changes.
- Keep detailed notes of what you've tried so far to avoid repeating the same steps.
- Don't hesitate to ask for help if you're stuck. There are plenty of forums and communities where experts are happy to assist.
Advanced Tips for Persistent Issues
Still having trouble? Let's dive deeper into some advanced troubleshooting techniques:
Regenerate Your SSH Keys: If all else fails, consider regenerating your SSH keys. This involves creating a new key pair and replacing the old one on both the client and server sides. Be careful, though—this can disrupt existing connections if not done properly.
Update Your SSH Client: Outdated SSH clients can sometimes cause compatibility issues. Make sure you're running the latest version of OpenSSH or whichever client you're using.
Using SSH Agent Forwarding
SSH agent forwarding allows you to use your local SSH keys to authenticate with other servers. This can be especially useful if you're managing multiple devices through a single RemoteIoT platform. To enable it, add the -A flag when connecting via SSH, like this: ssh -A user@server.
Best Practices for Managing SSH Keys
Managing SSH keys effectively is key (pun intended) to maintaining secure connections. Here are some best practices to follow:
- Use Strong Keys: Always generate keys with a sufficient length (at least 2048 bits for RSA).
- Protect Your Private Key: Store your private key in a secure location and use a passphrase to protect it.
- Limit Key Access: Only share your public key with trusted systems and revoke access when necessary.
- Regularly Audit Keys: Periodically review your SSH keys to ensure they're still valid and necessary.
Key Rotation Strategies
Just like passwords, SSH keys should be rotated periodically to minimize the risk of compromise. Develop a key rotation strategy that works for your team, and make sure everyone is on board with the process.
Security Considerations for SSH Keys
Security should always be a top priority when working with SSH keys. Here are a few things to keep in mind:
Enable Two-Factor Authentication (2FA): Adding an extra layer of security can significantly reduce the risk of unauthorized access. Many RemoteIoT platforms support 2FA, so take advantage of it if available.
Monitor Access Logs: Keep an eye on who's accessing your devices and when. Unusual activity could indicate a potential security breach.
Common Security Pitfalls to Avoid
Here are a few common mistakes to avoid:
- Leaving default SSH settings unchanged.
- Using weak or predictable key passphrases.
- Failing to revoke keys when employees leave the organization.
Tools You Need for Efficient Troubleshooting
Having the right tools can make troubleshooting SSH issues much easier. Here are a few that we recommend:
- SSH Keygen: Use this tool to generate new SSH key pairs.
- SSH Agent: Simplifies key management by storing your private keys in memory.
- Log Analyzers: Tools like Log2Ram can help you analyze SSH logs for errors and warnings.
Automating SSH Key Management
For large teams or organizations, managing SSH keys manually can be a nightmare. Consider using automation tools like Ansible or Puppet to streamline the process.
Real-Life Examples of SSH Key Failures
To give you a better understanding of how SSH key issues can impact real-world scenarios, here are a couple of examples:
Example 1: A developer accidentally overwrites their SSH key while updating their system. Suddenly, they can't access their RemoteIoT platform anymore. After some troubleshooting, they realize the public key on the server is outdated and needs to be replaced.
Example 2: A network administrator notices unusual activity in the SSH logs. Upon investigation, they discover an unauthorized SSH key had been added to the authorized_keys file. They quickly remove the key and implement stricter access controls to prevent future incidents.
Wrapping Up: Your Next Steps
And there you have it—a comprehensive guide to fixing your RemoteIoT platform SSH key issues. Whether you're dealing with permission problems, key mismatches, or network glitches, the tips and tricks we've covered should help you get back on track. Remember, SSH keys are a powerful